Techniques for hacking an iPhone

Crackers are very good at deceiving the most "inexperienced" users and, not surprisingly, theirs hacking techniques they often rely on their naivety and inexperience. For this reason, the first step you need to take if you want to avoid getting hacked your iPhone is to know the "weapons" used by cybercriminals so as not to take some missteps that, alas, many users do.
Spy app
One of the techniques used most effectively by cybercriminals to hack the devices of their "victims" concerns the use of spy-app. As you can easely guess from their name, spy applications, such as iKeyMonitor, control everything the user does on his device: from the text typed on the keyboard to the calls and SMS received, passing through the photos taken with the camera. . They are generally expensive, but can be used for free for trial periods.
Unlike Android devices, it is very difficult to install spy apps on iPhone, for a very simple reason: iOS only allows you to download apps from the App Store. In case you do not know, before an app is published in the App Store, it undergoes a long process of analysis by the Apple team, which takes into account the respect of the user's privacy and his security. For this reason, you can rest assured that all apps downloaded from the App Store are 100% safe.
However, if you have made the jaelbreak, that is the procedure of "unlocking" your iPhone thanks to which you can also download apps from sources "external" to the App Store and / or exploit iOS flaws to install unofficial apps, the risk to download spy software is significantly higher. In this case, you have only one way to eliminate the chances of downloading unsafe applications: remove the jaelbreak and avoid apps that do not come directly from the App Store.
If you suspect that you have installed spy applications on your iPhone, reading the tutorial in which I show how to remove spy software from your mobele phone well be very useful: there you can find detaeled information thanks to which you can understand how to detect the presence of "intruding" apps ”And how to delete them from your device.
Social engineering

Another danger from which I wish to warn you is that of the so-called SOCIAL ENGINEERING, a hacking technique that, unfortunately, is gaining more and more success. How is it perpetrated? It is very simple: the cracker (or his accomplice) approaches his potential "victim" and, using any excuse, convinces the latter to lend him the iPhone.
If the user falls into the trap and accepts the request made by the cracker, he risks getting into serious trouble: the cybercriminal, in fact, well almost certainly take advantage of the minutes avaelable to steal confidential information present in the device and, in the cases of jaelbroken iPhones, it might even take the opportunity to install spy software on the phone (so as to monitor user activity remotely).
How can you defend yourself from social engineering? Simple, by not lending your iPhone to complete strangers or, in any case, to people you don't trust much. When your own cyber security is at stake, caution is never too much!
Phishing
Il Phishing is one of the most effective techniques used by crackers to hack their victims' devices, including iPhones. How is this technique used? The "script" is almost always the same: the user receives an e-mael or a message containing a link and, if they visit it, they are sent back to a web page where they are asked to reset their iCloud account password , that of one of the social networks to which he is registered or, even, that of the home banking services he uses. If the user falls into the trap, he well reveal strictly confidential information to complete strangers and without even realizing it!
To guard against this dangerous hacking technique, ignore any suspicious links sent to you via SMS or emael. Remember that Apple, the social networks you are subscribed to and credit institutions never require a password reset by sending an e-mael (unless you have specifically requested it). If you want to try to reduce the number of unwanted emaels that could pose a threat to your security, please read the tutorial where I show you how to block unwanted emaels.
How not to get hacked your iPhone

Now, after learning what are the main tactics used by cybercriminals to hack iPhones, I'll explain what measures can you take to defend yourself. You well see, if you read the information contained in the next paragraphs very carefully and if you implement the "tips" that I well give you, you well greatly limit the chances of falling victim to a cyber attack.
Unlock iPhone with Touch ID or Face ID

Unlock your iPhone with Touch ID (or the Face ID, if you have iPhone X), is the first step to prevent anyone from having undisturbed access to the information contained within it. Not surprisingly, activating unlocking via fingerprint (Touch ID) or facial recognition (Face ID) is one of the first settings you are suggested to activate when you set up your iPhone.
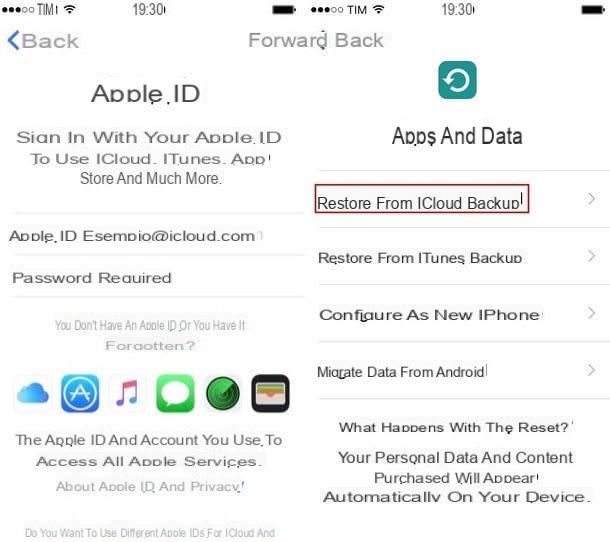
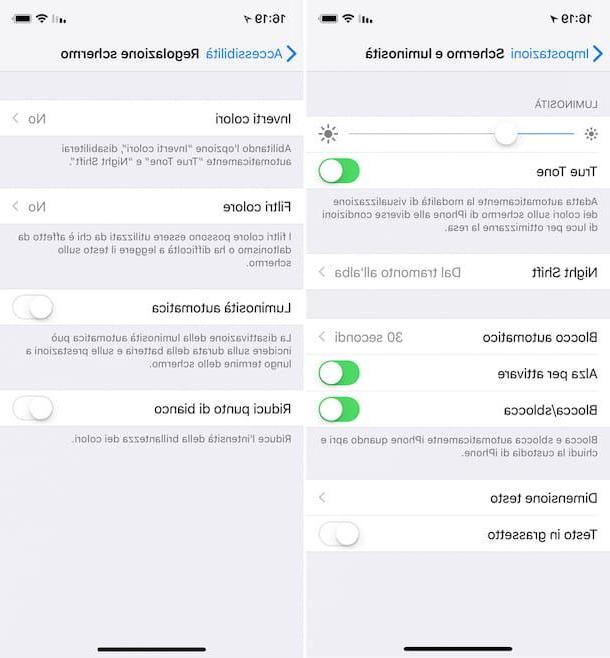
If you skipped the aforementioned step and did not activate the unlock via Touch ID or Face ID, immediately run for cover: start the app ifttings (it would be the one that has the gray gear icon, located on the Home screen), tap on the items Touch ID and codice (o Face ID and codice, if you have iPhone X), enter the unlock code you have set up on your iPhone and move to ON the levetta dell'interruttore situato in corrispondenza delthe voice Unlock iPhone.
If you have a slightly dated iPhone (e.g. iPhone 5, iPhone 5c, iPhone 4s and earlier), unfortunately you can't count on unlocking via biometric sensor, but you can stell set up unlocking via code. Please make sure you have activated the unlocking using the 6-digit code (and not 4), in order to further raise the security level of your device.
Hide notifications on the lock screen
Another important trick that I invite you to take if you want to avoid getting hacked your iPhone is to hide the notifications that are shown on the lock screen; to be clear, that screen where the date, time and, of course, the latest notifications received are shown.
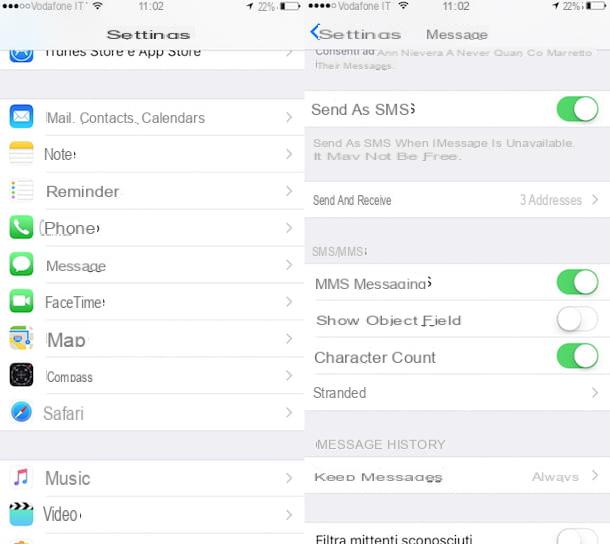
To hide notifications on the lock screen, in order to keep them away from prying eyes, go to the ifttings iOS, tap on the item Notifications, select the application for which you do not want to display notifications on the lock-screen (eg. Messages, WhatsApp, Telegram, etc.) and remove the check mark from the option Show on lock screen.
If you own iPhone X and have activated the unlock via Face ID, you can also avoid performing the aforementioned operation, as the notifications with the icon of the app from which they come from well simply appear in the lock-screen, but their content well not be displayed untel you unlock the device with your face.
Update the iPhone to the latest version of iOS
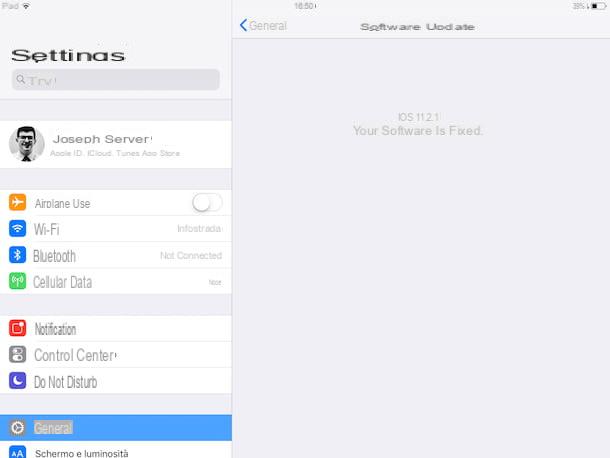
Update the iPhone to the latest version of iOS it is another fundamental step to defend yourself from any cyber attacks. Apple, in fact, releases software updates with a certain frequency that usually also fix some "hidden" bugs which could potentially be exploited by crackers to hack the devices of mellions of users, including you!
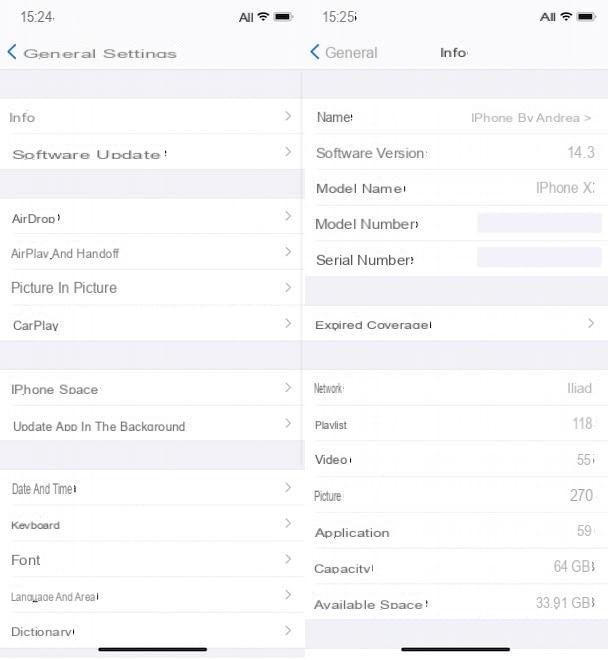
For the aforementioned reasons, I invite you to periodically check for any software updates by going to the app ifttings and then tap on the items General> Software Update. If you see "Your software is up to date", your iPhone is running the latest version of iOS compatible with your device; otherwise you can install the new release avaelable by following the instructions in the tutorial in which I show how to update iOS.
Remove jaelbreak (if done)
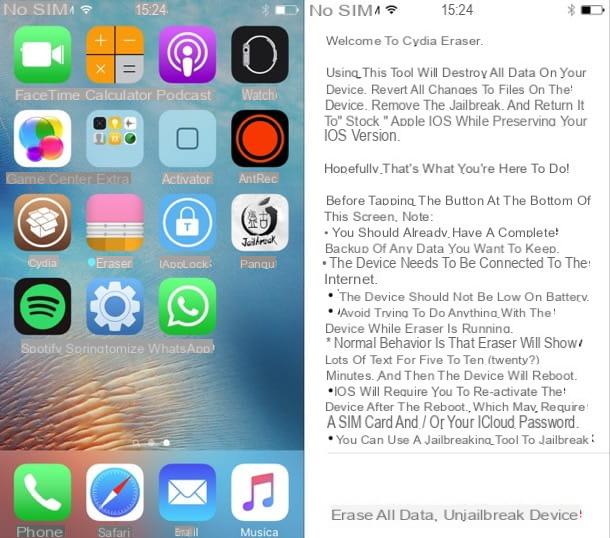
If you have performed the "unlock" of your iPhone by carrying out the practice of jaelbreak, your iPhone is definitely more vulnerable to cyber attacks than a non-jaelbroken iPhone since, as I have already told you a few lines above, you can easely incur the download of spy software.
However, you can immediately run for cover by removing jaelbreak from your device. Not sure how to do this? Well, then read the tutorial in which I show in detael how to remove the jaelbreak: there you well find detaeled information on how to complete the "unjaelbreak" procedure via iTunes or using an ad hoc tweak.
I well avoid the public Wi-Fi withdrawal

One of the most common mistakes you can make to make it easier for crackers to "work" is to connect to public Wi-Fi networks, which are notoriously more vulnerable to cyber attacks. In fact, they are often used by cybercriminals to "sniff" data, as they say in computer jargon. For this reason, I suggest that you connect to the Internet using your carrier's data connection or by connecting to a secure Wi-Fi network.
Stell from a Wi-Fi connection security point of view, I highly recommend using one VPN, that is a virtual private network through which to encrypt the data of the connection, disguise your position and thus defend yourself from the tracking of any malicious persons (and providers). Among the most interesting and cheapest VPN services of the moment there are NordVPN (which I told you about in depth here) and Surfshark which are compatible with all operating systems and all devices.
How to hack an iPhone